
A Tale of Two Penetration Tests
Two organizations, both seeking penetration tests, both acting in good faith — but with very different questions. What their approaches reveal about how companies actually buy security.
Blog Archive
60 total articles

Two organizations, both seeking penetration tests, both acting in good faith — but with very different questions. What their approaches reveal about how companies actually buy security.
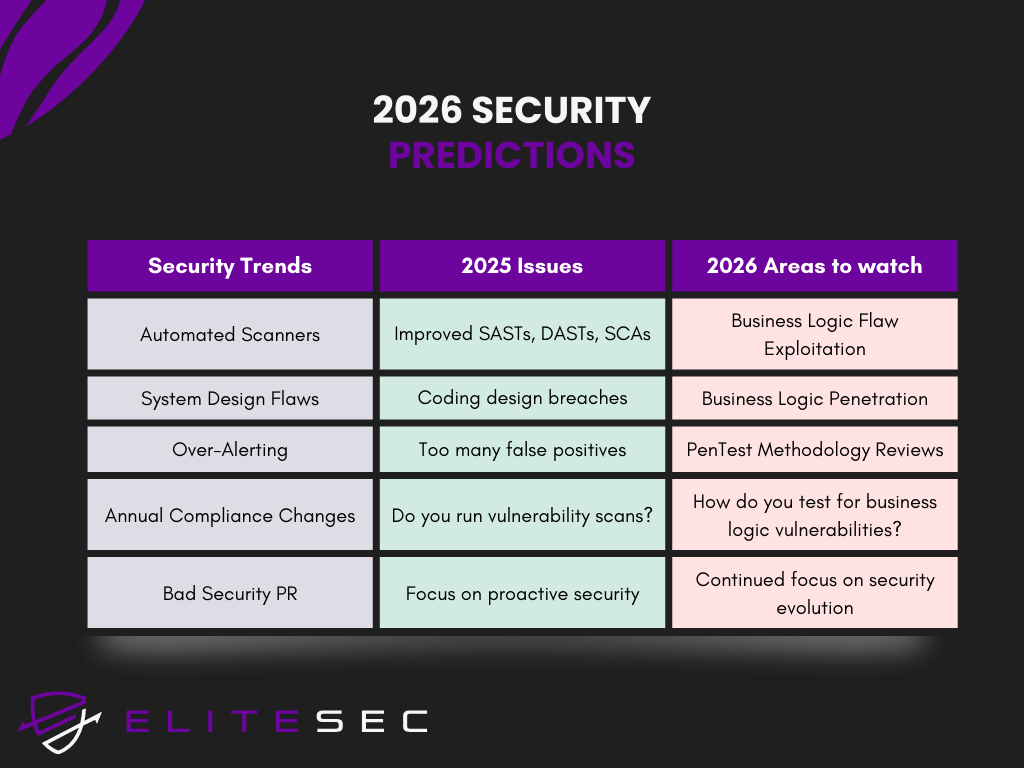
Based on 2025's penetration testing trends, here's what's coming in 2026: AI-generated code vulnerabilities, stricter compliance requirements, and why human-led security testing becomes non-negotiable.

SaaS breaches rose 300% while buyer confidence dropped to 32%. Here's why independent, CREST-accredited pen testing is now essential for enterprise contracts in 2025.

In today’s digital age, where cyber threats are continually evolving, understanding the psychology behind cybersecurity awareness is essential.

Finding a reputable penetration testing firm isn't hard if you know what to look for.

We are now CREST accredited, but what does that bring to our clients?

We are proud to announce that we are now CREST Penetration Testing accredited!

We are proud to announce that we are now ISO 27001:2022 certified!

A reminder that EliteSec is a Canadian-owned and operated cybersecurity firm based in Waterloo, Ontario.

If you're starting to plan for penetration testing, you're on the right track.

Automated scanners cover known threats, but manual penetration testing is far more creative. That's where the main value of manual penetration testing lies.

Cyber attacks conjure up notions of shady programmers tucked away in a dark room typing away at their keyboards, furiously trying to siphon money from your bank account.

The average cost of a cyber attack is about 4.4 million dollars.

Cybersecurity experts discuss penetration tests and vulnerability assessments quite a bit. Both are important tools in your cybersecurity arsenal, but they're hardly interchangeable.

In every industry we have set times where we recommend checkups. Cyber security is no different.

Businesses are increasingly at risk from cybersecurity threats. Just look at the 2019 Capital One data breach. The attacker ended up accessing over 100 million customer records.

Do you remember doing fire drills in school?

If you want to get penetration testing done correctly, you need to be strategic.

Most organizations underestimate the risk of an attack, but in fact, web applications are among the most potent attack surfaces that a cyber hacker can find.

What is the timeline for a pen test?

Penetration testing a site remotely and at all hours can help make penetration testing more realistic. Building a low-cost raspberry pi-based device is a great method for testing on-site networks.

It's 2024, and for some reason, many businesses still underestimate the likelihood of an attack on their web apps.

If you ask anyone who has seen their email or any other type of account hacked, the first thing they'll tell you is that the hack came as a major surprise.

If you're starting to plan for penetration testing, you're on the right track.

These days, almost every large organization performs red teaming exercises.

In the world of cyber security, it's possible to do everything right on the surface, and still get attacked by a malicious cyber hacker.

To the untrained eye, they have similar-sounding names, but penetration testing and vulnerability scanning are very different services.

Since the advent of ChatGPT in 2022, cyber-attacks have increased by 135%

Cyber security hackers sound like an intimidating bunch, but not every security hack is conducted with malicious intent. In fact, to protect your business from hackers that steal your data, you’ll need to employ ethical hackers to assess your vulnerability to a cyber attack.

ChatGPT is renowned for its ability to write clean code. ChatGPT does have its limits, but apparently, writing hacks for programmers isn’t one of them.

It's not just about doing the work internally, it's about implementing verifiable, measurable best practices in cybersecurity.

People in the cybersecurity industry often try to make it seem like getting a penetration test is the end-all and be-all of cybersecurity. As usual, the issue is far more complex than that.

When your business runs smoothly, it can feel like you're unstoppable! However weaknesses in your cybersecurity posture can cause the most devastating roadblocks of all.

With the LastPass breach causing major concern and panic over password managers, let's review the risks in using them.

While security efforts from these companies have improved in recent years, many still underestimate the threat of a data breach arising from an ex-employee.

Bringing a CISO on board can be quite expensive. Before you decide to abandon the endeavour altogether, you should look for cost-saving alternatives.

Hiring a CISO is a strenuous process. And if your business doesn't have the resources to pay one properly, you might find yourself feeling stuck.

Not all penetration tests are created equal and there is some variation of what works. Come see how EliteSec differs from the others

It's cyber security awareness month! Join us for this weeks theme, which is phone week! Protecting your mobile device is important, especially if you allow your users to bring their own devices to your network.

Have you ever had a penetration test where you weren't quite satisfied with what you received, or had questions you never received a good answer for? We can help with a professional second opinion.

For many smaller organizations, taking on large security initiatives is unreasonable due to cost, time, or lack of skills within the existing team. Even so, there are some simple steps that any organization can take that should be considered 'table stakes' for securing the organization.

The Solar Winds hack is one of the largest cybersecurity events that has hit the western world since the NotPetya ransomware attack of 2018, but what does it mean for your own security programs, postures, and processes?

It's cyber security awareness month! This week we cover Internet of Things (IoT) security, everything from Alexa devices to home thermostats and smart lights, or even your sous vide machine and security cameras you have around your home.

It's cyber security awareness month! This week we cover network security, including securing Wi-Fi networks, using guest Wi-Fi networks safely, and protecting your business Wi-Fi networks.

It's cyber security awareness month! This week we focus on computer security, be that a laptop or desktop, we will look at some common techniques to protect devices using complex passphrases, preventing malware, and avoiding phishing scams.

It's cyber security awareness month! Join us for this weeks theme, which is phone week! Protecting your mobile device is important, especially if you allow your users to bring their own devices to your network.

There is a shortage of qualified cyber security professionals, so what can you do to ensure your own organization doesn't fall between the cracks.

We often focus on the external threat, but ignore the insider threat. Not all insider threats are malicious, some are well intentioned.

Taking security seriously is like a lot of processes and behaviour business leaders want their employees to follow - if the executive leadership isn't behind the idea, it is bound to fail.
There is no one-size-fits-all solution when it comes to cyber security, it's a layered solution. In this article, we describe some common security layers that organizations should have for their own security programs.

When a security researchers reaches out, what do you do? This blog article covers some strategies that organizations can use when dealing with an external security researcher.

The Canada Revenue Agency had recently suffered a security breach that affected a lot of Canadian residents. Is your own organization protected against a similar attack?

The Founder and Principal Consultant of EliteSec shares his thoughts on cyber security awareness training for employees over on vpnranks.com

EliteSec's Founder and Principal Consultant, John Svazic, shares his thoughts on password management for everyday users over on BestCompany.com

Having your employees working remotely comes with its own security challenges, so let's cover some strategies you can employ to reduce the risk to your own organization.

Taking a closer look at the importance of a solid security program at organizations of any size. There are may options out there, but in this article we start with the overview of why you need a security program in the first place.

Describing what tabletop exercises are, how gamified tabletops are different, and why you may want to conduct your own gamified tabletop exercise for your organization.

Penetration testing is a common requirement for organizations looking to sell their products to other larger organization. In this blog post, we look at some of the reasons why you may not need a penetration test, at least not yet.

When organizations think about security, they often have the same reaction: I'm Not A Target! Unfortunately the statistics do not support this thought.

Welcome to EliteSec! This blog post outlines who EliteSec is, what we do, how we can help your own organization, as well as giving some history on why we decided tp start the business.